Digitization
IT & information security
Safety and responsibility for today and tomorrow
In an increasingly networked world, cyber security and digitalization are indispensable components of modern technologies and processes in the manufacturing industry. Innovative solutions lead companies securely and efficiently into the digital future. The decisive factor here is the first step, which we are happy to assist you with.
Our expertise ranges from the implementation of highly secure IT infrastructures to the development of tailor-made digitalization solutions that optimize and protect your business processes.
Cyber Security
- Risk assessment of the current IT
- Network Analysis
- Automated anomaly detection
- Prevention
- Consulting services for ISO 27001 and BSI basic protection
- Implementation of ISMS and PSIM (information security management systems and physical security information management)
- Advice on IEC 62443 for a secure OT environment
- (Industrial) Cloud
- IaaS
- SaaS
- AI
- Modern dashboarding
- Paperless processes
- Consulting for digitization strategy
IT and OT
- Hardware
- Network technology
- Infrastructure services
- Automation infrastructure
YOUR CONTACT PERSONS
What can we do for you?
Please call or email us.
We are looking forward to your inquiry.
Sven Ebbinghaus
Site Manager MAR South
Digitization | Information security
MAR Marine and
Automation technology Rostock GmbH
Hundsburgallee 9c
18106 Rostock
Laws and standards
In today's digital era, where IT and OT are increasingly interconnected, cyber security is critical. Companies need to protect their infrastructures from a wide range of threats, from simple malware to targeted attacks.
NIS 2.0
Cyber security of network and information systems
CRITIS
Classification via entrepreneurs who are personally liable
IEC 62443
Regulates industrial communication networks and IACS
ISO 27001
Defines basic IT protection
Innovations announced by the federal government
The new NIS-2 Regulation changes legal measures to increase the overall level of cybersecurity in the EU.
Our service portfolio
Of course, we also support you in the area of physical security by integrating a Physical Security Information Management System, or PSIM for short.
01
Assesment
- Network and infrastructure security
- Access and identity management
- Endpoint and device security
- Data and communication security
02
GAP analysis
- Actual state
- Definition of target state
- Identification and analysis of security gaps (GAPs)
- Development of measures to close the GAPs
03
Roadmap
- Creation of a detailed roadmap with a timetable for implementing immediate measures and long-term security solutions
- Monitoring and documentation
04
PoV
- Implementation of immediate measures and, if necessary, long-term security solutions
- Definition of relevant KPIs
- Collection of baseline data through security assessments, penetration tests and system monitoring
- Continuous monitoring of the effectiveness of the measures
- Preparation of a detailed report
05
Rollout
- Creation of rollout plan with phases, schedules and milestones for the entire organization
- Implementation of all measures in accordance with the rollout plan
- Involvement of all stakeholders
06
SOC/Operation
- Establishment and optimization of a Security Operation Center (SOC)
- Continuous monitoring and threat detection
- Incident response and management
- Patch and vulnerability management
- Employee training
- Compliance with legal requirements
Digital transformation
Digitalization in the manufacturing process environment
Digital business processes refers to the networking of all levels of the automation pyramid to increase the efficiency and productivity of your company and is therefore a key component of digital transformation. With IoT technologies, the classic levels of the pyramid are dissolved and transferred to a uniform namespace. This enables genuine networking of all devices.
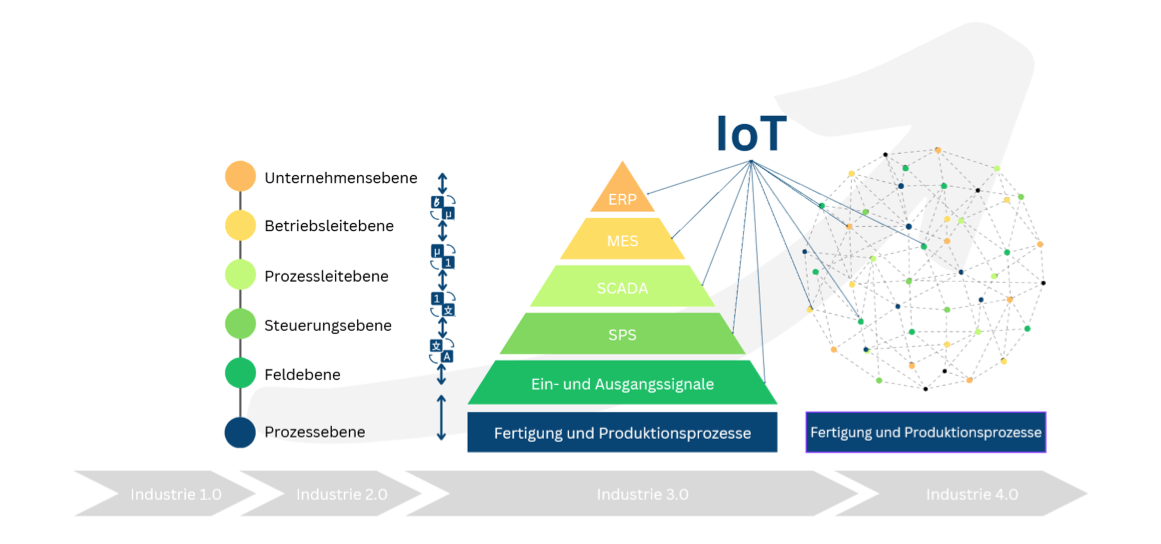
They enable
Increased transparency
Flexibility to work from any location
Better cooperation
Increasing efficiency
We provide you with software-independent advice on implementation and, if required, support from a strictly hierarchical model to a defined namespace. We are happy to take over the implementation and customizing for your tailor-made solution on premise or in the cloud.
IT infrastructure and network technology
We offer comprehensive solutions for your entire IT infrastructure on premise or as IaaS (Infrastructure as a Service)
- High-quality hardware
We sell and install state-of-the-art IT and OT servers, workstations and network components
- Reliable network technology
We plan a robust network architecture tailored to your needs and implement it on request. High-availability switches, routers and firewalls optimize your infrastructure in terms of security and availability.
- Infrastructure services
Professional backup and disaster recovery solutions help you to continue production or operations quickly in an emergency.
- Consulting and network topology
We work with you to analyze and develop your future-proof network topology, taking into account all applicable security standards.
- Installation and setup of operating systems
Linux or Windows-based operating systems
